SSH Two Step Authentication with google-authenticator
What is Two step authentication? You all already know it. Just try to login to your facebook account and after you enter your username and password you will be notified to enter code from facebook code generator.
Are you asking why should I care? If you write lastb command into your terminal, you will probably get similar results. About 8 unsuccessful ssh logins per minute to server. And as notice, all with root username. So first big step forward secured server? Set PermitRootLogin to no in your /etc/ssh/sshd_config! I sounds stupid, but almost 90% of all brute force attacks are with root username. But what next? You know, just because I’m paranoid doesn’t mean they’re not out to get me.

We will install google-authenticator to have dreamless sleep. That is as easy as write this command:
sudo apt-get install libpam-google-authenticator
And then we run it:
google-authenticator
You will get similar result. This QR code is you secret, so don’t upload it to you blog as I :-). You can use any of two step authentication app you like, I do use OTP Auth, to scan it and get your time dependent password generator.
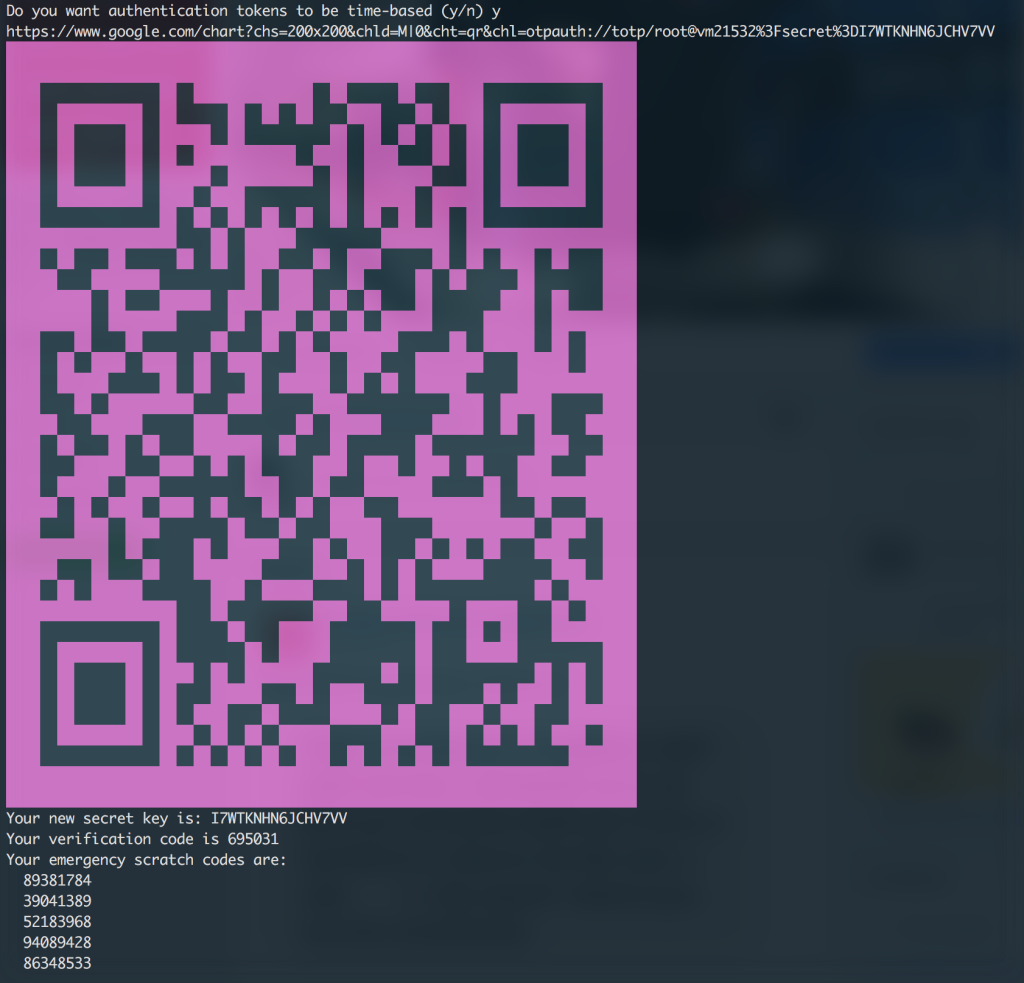
Do you want me to update your "~/.google_authenticator" file (y/n) y
Then you will be asked about your prefered settings. First if you want to, disallow code reuse. I recommend to answer yes.
Do you want to disallow multiple uses of the same authentication token? This restricts you to one login about every 30s, but it increases your chances to notice or even prevent man-in-the-middle attacks (y/n) y
Then if want to increase your code valid-time interval. If you don’t expect your slippage between your client and server I reccomend answer no.
By default, tokens are good for 30 seconds and in order to compensate for possible time-skew between the client and the server, we allow an extra token before and after the current time. If you experience problems with poor time synchronization, you can increase the window from its default size of 1:30min to about 4min. Do you want to do so (y/n) n
And finally if you want to accept only 3 logins every 30s. And that depends on your use case. Because I’m the only user of my server, I don’t expect there will be more than 3 logins in 30s interval.
If the computer that you are logging into isn't hardened against brute-force login attempts, you can enable rate-limiting for the authentication module. By default, this limits attackers to no more than 3 login attempts every 30s. Do you want to enable rate-limiting (y/n) y
Now we have google-authenticator installed and we have to set our sshd to require two step authentication. So edit /etc/pam.d/sshd with your favourite editor.
nano /etc/pam.d/sshd
And add this line (When you put it at the top, SSH will first ask a verification code, then a password.):
auth required pam_google_authenticator.so
If you want two step verification to be optional, that means that you have users that didn’t initialized google-authenticator on their accounts and you want to allow them to login add nullok.
auth required pam_google_authenticator.so nullok
Last thing we have to do is tell ssh to ask for verification code. That setting is located in:
nano /etc/ssh/sshd_config
Where you have to set:
ChallengeResponseAuthentication yes
Know restart ssh service and you done!
sudo service ssh restart
As you can see, two step authentication is quite easy to configure and it offers much more than securing your ssh. E.g. you can secure your desktop login too. And moreover it’s for free 🙂
 Out of coffee 😱, please help!
Out of coffee 😱, please help!
